Threat Investigation Platform
Are you facing increasingly frequent and sophisticated cyber threat ? Are you looking to make your investigation easier and faster ? Do you want to optimize the work of your experts and ease collaboration?
Search no more, Defants vSIRT is a Threat Investigation Platform enabling you to modernize how to deal with threats in your SOC or Incident Response team. Defants vSIRT automates and pushes back the limits of traditional investigation software.
Choose for

Automated analysis and scoring
based on the MITRE ATT&CK framework to identify and qualify threats, with or without indicators of compromise.

Semantic investigation
to explore your data as a knowledge graph and discover complex attack paths.

Real-time collaboration
to share information and actions between your experts, generate reports and attack timeline.
Defants vSIRT by its users
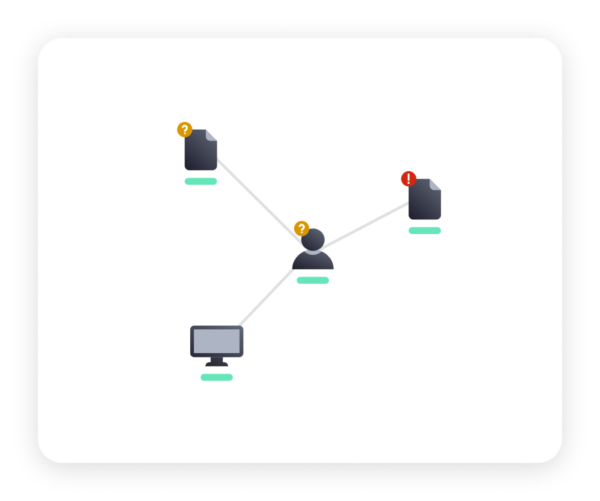
Use semantic graph to pivot from threat actor information
Get immediate access to a visual representation of the relationships within a semantic graph while Defants vSIRT still analyzes and correlates the various data sources to maximize your time.
Find Indicators of Compromission in minutes with knowledge base like Mitre Att&ck, Yara and Sigma rules. Each visual representation within the graph contains all the original datas of your collection in a totally transpareny and comprehensible way for the analyst
Find your collaborative timeline in one place
Use our collaborative timeline to deep-dive into the attack scenario. Defants vSIRT gathers and consolidates all relevant time-based events from various data sources, giving you a step-by-step chronology of the threat actor’s behavior.
Easy to understand, manipulate and annote, it’s the perfect tool to rebuildthe exact chronology of the incident efficiently.
Collaborate in real time, from anywhere
Work in real time with your team on the same threat investigation. Track the progress of other analysts, view all notes and share results with your team in a single tool.
Work seamlessly across time zones, pursue 24/7 investigations and respond thrice more faster. Onboard your juniors and enhance their skills with all the collaborative tools right inside the platform. All your staff will never be left alone.
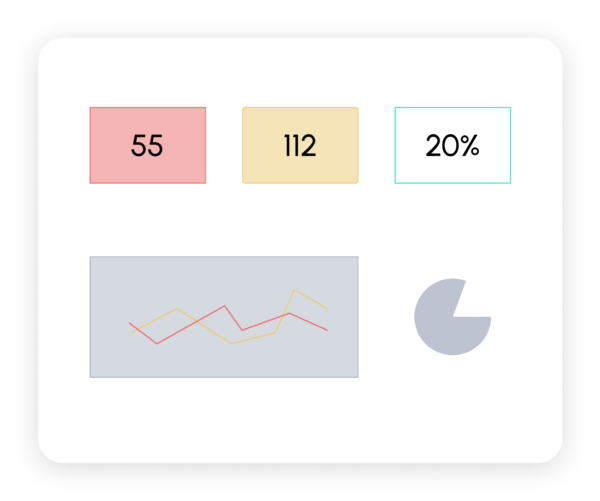
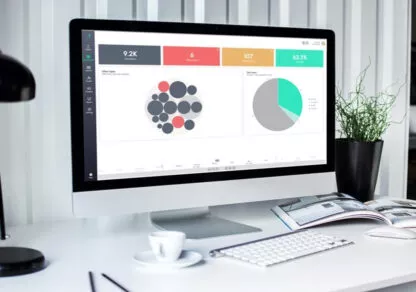
Keep track of the investigation’s progress
Track the progress of your threat investigation with clear, relevant indicators in the dashboard featuring key performance indicators such as malicious and suspicious items or the percentage of investigation progress.
Give your clients visibility on the recovery from the incident and balance your resources according to your needs.
Reduce report-writing time
Save your cybersecurity analysts time with pre-filled templates and AI-assisted report generation. Benefit from the automatic addition of all your team’s notes and tags, and create a thorough report.
All case informations you need are merged instantly in your report template, easy to edit and share.
They trust us
Related resources


















